| .gitignore | ||
| .screenshot.png | ||
| go.mod | ||
| go.sum | ||
| index.html | ||
| minipam.go | ||
| README.md | ||
MinIPAM
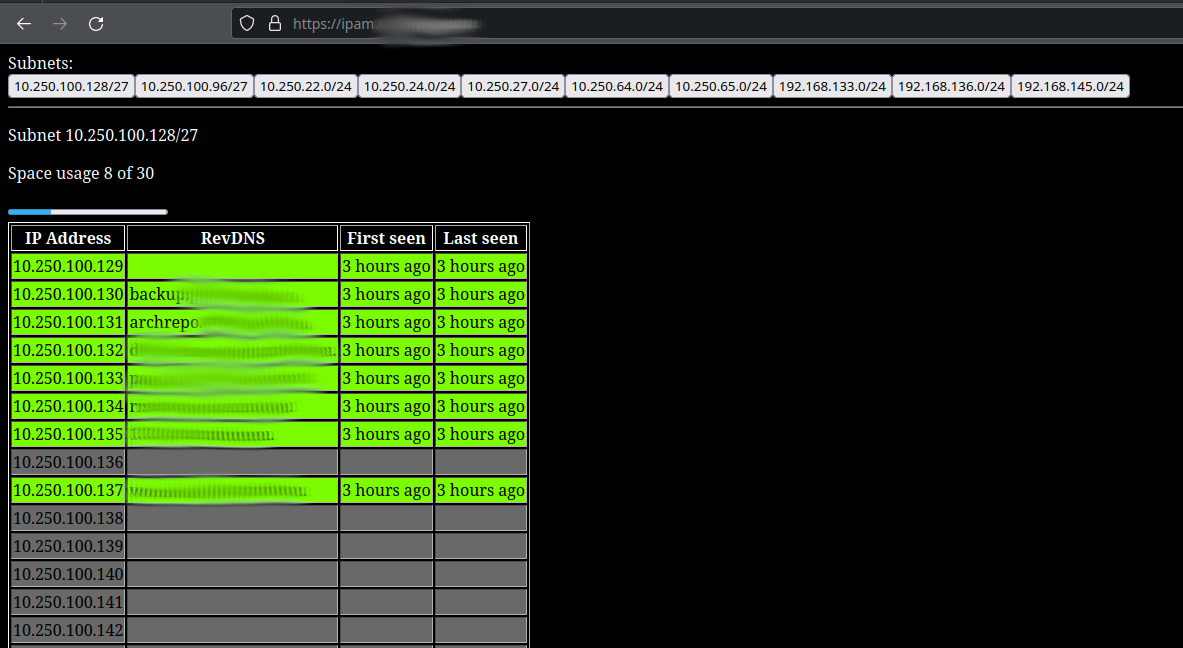
A simple tool that scans specified subnet(s) and has WEB UI to easily see which IPs are available
I wanted something like space map from PHPIPAM but with less clicking to get to see what I want to see. Web UI is just a bunch of buttons (one for subnet) and table, representing hosts in said subnet. Hosts that were online during last scan are marked as green, hosts which were online at least once but were offline during last scan are marked red, and hosts that were never seen online are marked gray. Also for every online host during a scan RevDNS lookup is made to attempt to get its hostname. Web UI does not allow editing presented data in any way, which is also why there is no authorization mechanism built in.
Scanning is kind of slow, but I prefer to keep it that way, since I don't need it to be fast, and I don't want to waste my compute resources. It doesn't matter for me if my scan completes within 1 minute or within 30 minutes.
Subnets are scanned in parallel, but addresses in each subnet are still scanned sequentially. So complete scan takes as much time, as scanning of biggest subnet that you have.
Compilation
Install go toolchain and run
go install git.mlody.eu/lmoskala/MinIPAM
Or, clone repository and run
go build
Cross-compiling is as easy as running GOOS=freebsd GOARCH=amd64 go build.
Configuration reference
bind_address: "0.0.0.0:8443"
scan_subnets:
- 192.168.145.0/24
- 10.250.100.64.0/27
delay_between_scans: 15m
#Setting this to absolute path seems like a good idea :)
persistence_location: "data.json"
#Don't scan network and broadcast address, usually you want to leave this set to true
exclude_special_addresses: true
use_tls: false
#IF use_tls is set to false, following two options are ignored.
#key and cert and fullchain can be in one file. In this case, specify the same file in both fields
tls_key_file: "key.pem"
tls_cert_file: "fullchain.pem"
delay_between_scans specifies time to wait between scans. For example 15m means that
scan starts at 17:43, takes 2 minutes, finishes at 17:45, next scan will start at 18:00
exclude_special_addresses excludes network and broadcast addresses from scanning and results.
With subnets in example above, those would be 192.168.145.0,192.168.145.255,10.250.100.64,10.250.100.95.
persistence_location indicates where data should be stored. It needs to be writable.
Requirements
Scanning is done by running:
exec.Command("ping", "-n", "-W", "0.2", "-c", "1", addr)
So you need OS that has ping command with those options.
Tested with GNU coreutils on archlinux. Also works on FreeBSD, however, FreeBSD's ping will wait 1 second instead of
0.2 seconds, making scanning networks with a lot of free IPs slower.
While we're at it, hosts are expected to reply within 0.2 seconds (except on FreeBSD, where ping is not accepting fractional timeout values). This is currently hard-coded.
Authentication
Since I don't think that any data presented by this tool would be considered sensitive, I didn't implement any authentication mechanism. If for some reason you decided that you NEED one, consider following options:
- Use firewall to only allow trusted networks to access this tool
- If this tool happens to be running on your workstation, bind it to localhost only
- Bind this tool to localhost only and use SSH port forwarding
- Set up reverse proxy with authorization, then bind this tool to localhost only.